« Jellyfin » : différence entre les versions
Aller à la navigation
Aller à la recherche
| Ligne 57 : | Ligne 57 : | ||
Maintenant l'interface de Jellyfin sera accéssible via <nowiki>https://</nowiki><font color = blue>IP_SERVEUR</font>:8920 | Maintenant l'interface de Jellyfin sera accéssible via <nowiki>https://</nowiki><font color = blue>IP_SERVEUR</font>:8920 | ||
== Vhost pour Reverse-Proxy == | |||
server { | |||
listen 80; | |||
listen [::]:80; | |||
server_name <font color = blue>jellyfin.exemple.net</font>; | |||
# Uncomment to redirect HTTP to HTTPS | |||
return 301 <nowiki>https://</nowiki>$host$request_uri; | |||
} | |||
server { | |||
listen 443 ssl http2; | |||
listen [::]:443 ssl http2; | |||
server_name <font color = blue>jellyfin.exemple.net</font>; | |||
# use a variable to store the upstream proxy | |||
# in this example we are using a hostname which is resolved via DNS | |||
# (if you aren't using DNS remove the resolver line and change the variable to point to an IP address e.g `set $jellyfin 127.0.0.1`) | |||
set $jellyfin 192.168.2.209; | |||
ssl_certificate /etc/letsencrypt/live/<font color = blue>jellyfin.exemple.net</font>/fullchain.pem; | |||
ssl_certificate_key /etc/letsencrypt/live/<font color = blue>jellyfin.exemple.net</font>/privkey.pem; | |||
include /etc/letsencrypt/options-ssl-nginx.conf; | |||
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; | |||
add_header Strict-Transport-Security "max-age=31536000" always; | |||
ssl_trusted_certificate /etc/letsencrypt/live/<font color = blue>jellyfin.exemple.net</font>/chain.pem; | |||
ssl_stapling on; | |||
ssl_stapling_verify on; | |||
# Security / XSS Mitigation Headers | |||
add_header X-Frame-Options "SAMEORIGIN"; | |||
add_header X-XSS-Protection "1; mode=block"; | |||
add_header X-Content-Type-Options "nosniff"; | |||
# Content Security Policy | |||
# See: <nowiki>https://</nowiki>developer.mozilla.org/en-US/docs/Web/HTTP/CSP | |||
# Enforces https content and restricts JS/CSS to origin | |||
# External Javascript (such as cast_sender.js for Chromecast) must be whitelisted. | |||
add_header Content-Security-Policy "default-src https: data: blob:; style-src 'self' 'unsafe-inline'; script-src 'self' 'unsafe-inline' <nowiki>https://</nowiki>www.gstatic.com/cv/js/sender/v1/cast_sender.js; worker-src 'self' blob:; connect-src 'self'; object-src 'none'; frame-ancestors 'self'"; | |||
location / { | |||
# Proxy main Jellyfin traffic | |||
##proxy_pass <nowiki>http://</nowiki>$jellyfin:8096; | |||
proxy_pass <nowiki>https://</nowiki>$jellyfin:8920; | |||
proxy_set_header Host $host; | |||
proxy_set_header X-Real-IP $remote_addr; | |||
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; | |||
proxy_set_header X-Forwarded-Proto $scheme; | |||
proxy_set_header X-Forwarded-Protocol $scheme; | |||
proxy_set_header X-Forwarded-Host $http_host; | |||
# Disable buffering when the nginx proxy gets very resource heavy upon streaming | |||
proxy_buffering off; | |||
} | |||
# location block for /web - This is purely for aesthetics so /web/#!/ works instead of having to go to /web/index.html/#!/ | |||
location ~ ^/web/$ { | |||
# Proxy main Jellyfin traffic | |||
#proxy_pass <nowiki>http://</nowiki>$jellyfin:8096/web/index.html/$1; | |||
proxy_pass <nowiki>https://</nowiki>$jellyfin:8920/web/index.html/$1; | |||
proxy_set_header Host $host; | |||
proxy_set_header X-Real-IP $remote_addr; | |||
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; | |||
proxy_set_header X-Forwarded-Proto $scheme; | |||
proxy_set_header X-Forwarded-Protocol $scheme; | |||
proxy_set_header X-Forwarded-Host $http_host; | |||
} | |||
location /socket { | |||
# Proxy Jellyfin Websockets traffic | |||
#proxy_pass <nowiki>http://</nowiki>$jellyfin:8096; | |||
proxy_pass <nowiki>https://</nowiki>$jellyfin:8920; | |||
proxy_http_version 1.1; | |||
proxy_set_header Upgrade $http_upgrade; | |||
proxy_set_header Connection "upgrade"; | |||
proxy_set_header Host $host; | |||
proxy_set_header X-Real-IP $remote_addr; | |||
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; | |||
proxy_set_header X-Forwarded-Proto $scheme; | |||
proxy_set_header X-Forwarded-Protocol $scheme; | |||
proxy_set_header X-Forwarded-Host $http_host; | |||
} | |||
} | |||
Version du 13 octobre 2021 à 16:30
LXC Debian 11
Installation
# apt update && apt upgrade # apt install apt-transport-https gnupg lsb-release # wget -O - https://repo.jellyfin.org/debian/jellyfin_team.gpg.key | apt-key add - # echo "deb [arch=$( dpkg --print-architecture )] https://repo.jellyfin.org/debian $( lsb_release -c -s ) main" | tee /etc/apt/sources.list.d/jellyfin.list # apt update # apt install jellyfin
On peut sur rendre sur http://IP_SERVEUR:8096 pour vérifier le fonctionnement du service et faire la première configuration.
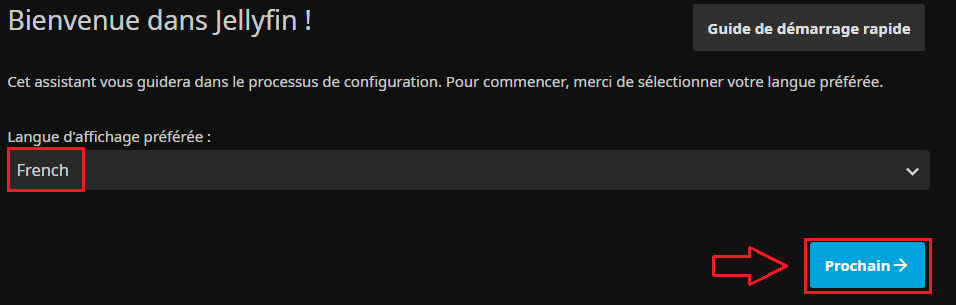
- On commence par le choix du langage préféré :
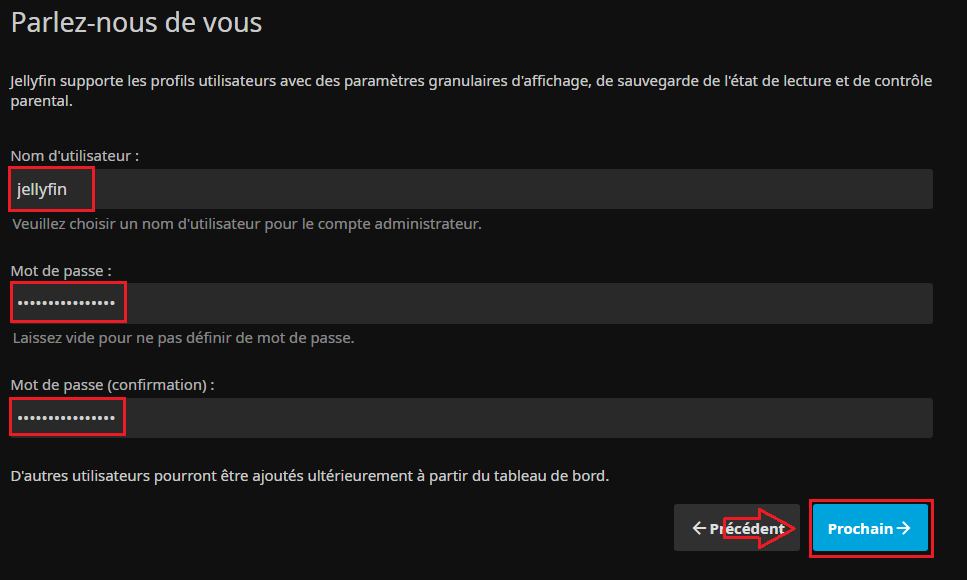
- On configure le compte d'administration et son mot de passe :
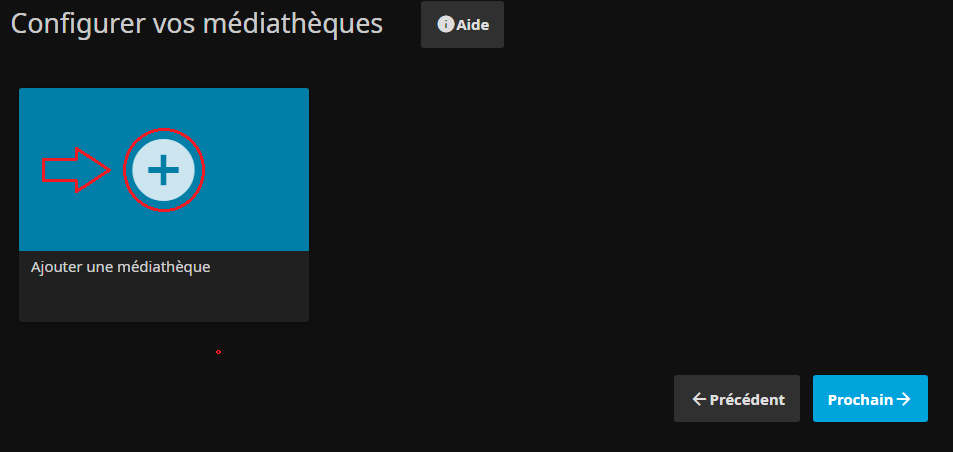
- On peut optionnelement inscrire tout de suite une ou plusieurs bibliothèques :
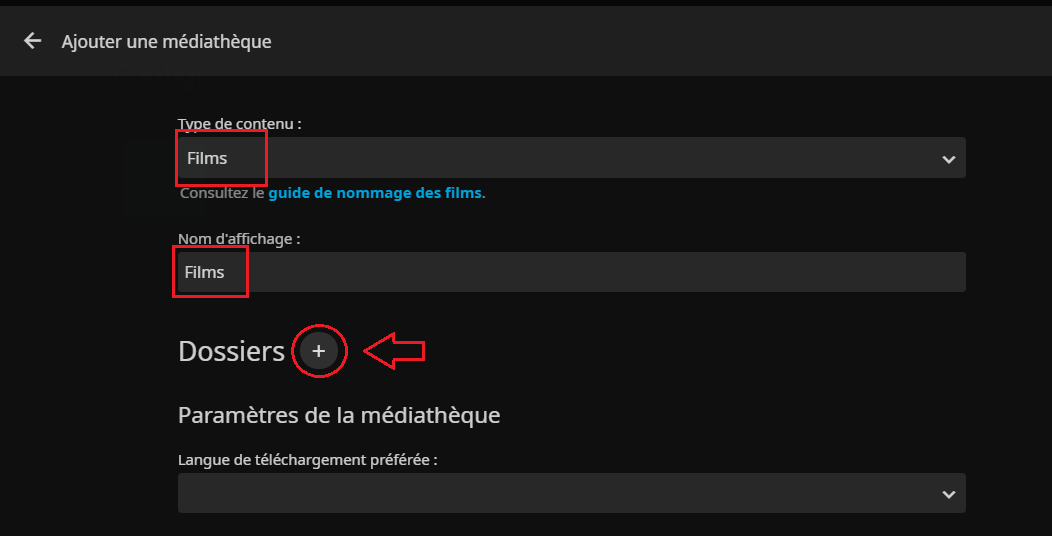
- Si l'on choisit d'ajouter une bibliothèque, on commence par choisir le type de médias et le nom, puis on choisit de configurer son emplacement :
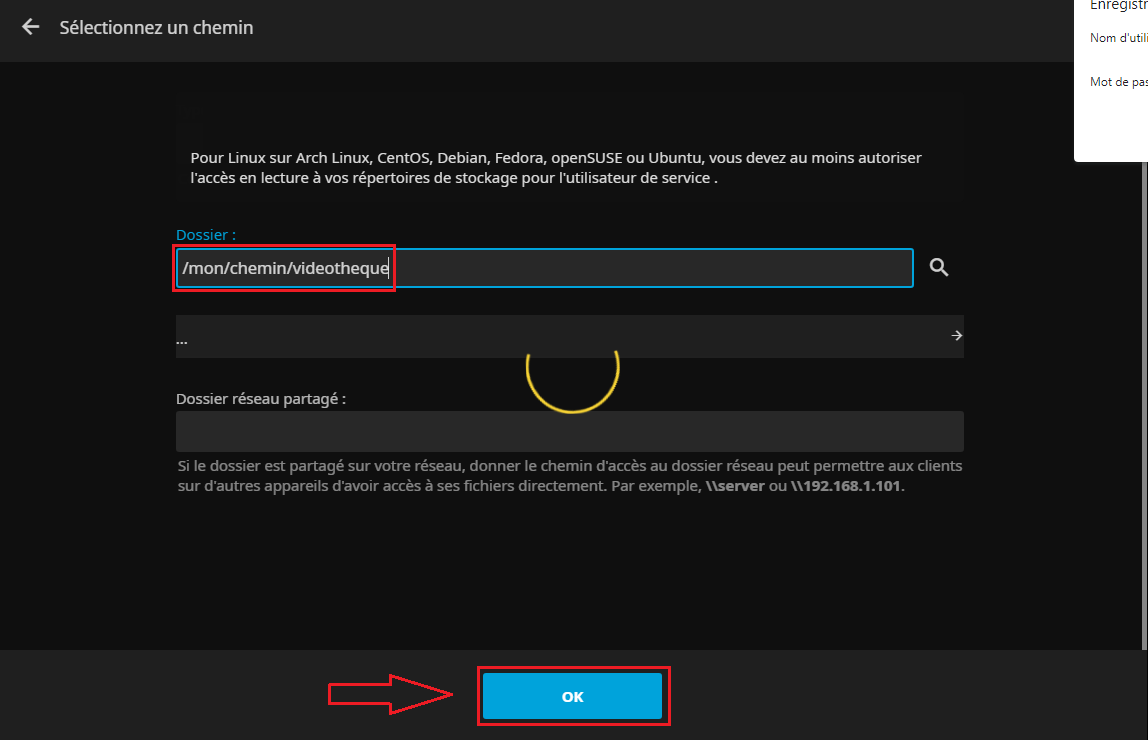
- On indique le chemin d'accès du dossier et on valide :
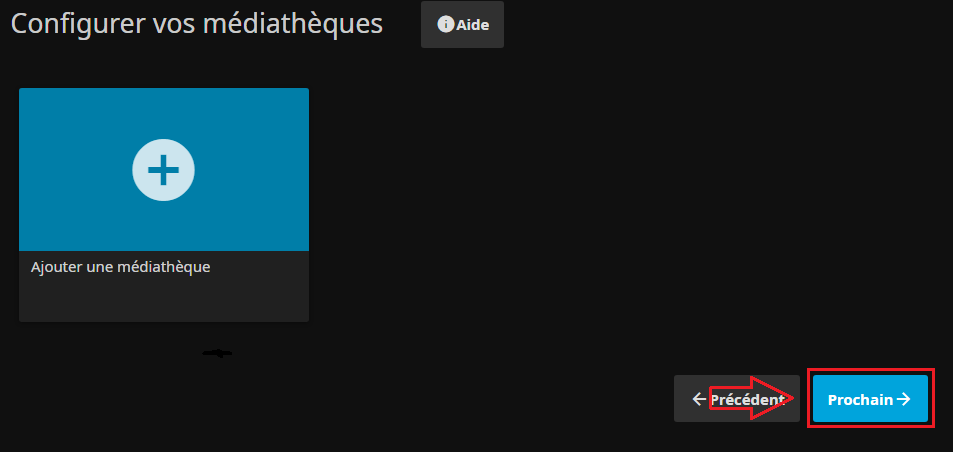
- Une fois la/les bibliothèques configurées ou laissées pour plus tard on pass à l'étape suivante :
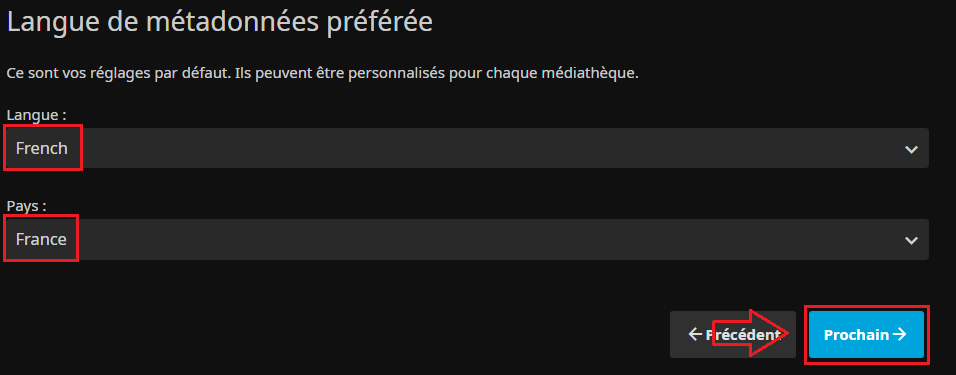
- Choix du langage par défaut pour les métadonnées :
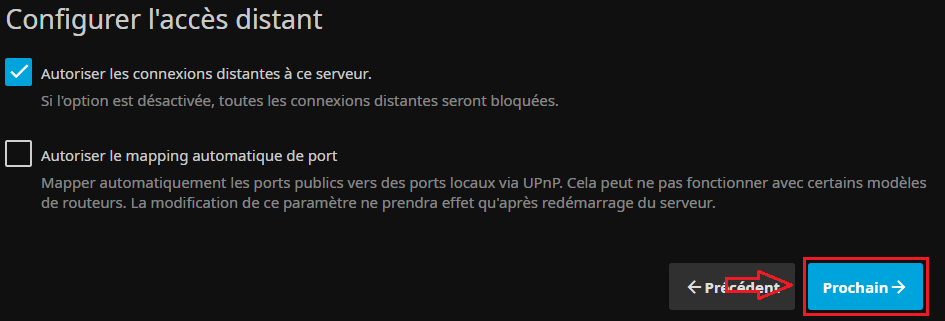
- On configure l'accès distant (a priori par défaut) :
- Le serveur nous indique que la configuration de base est terminé :
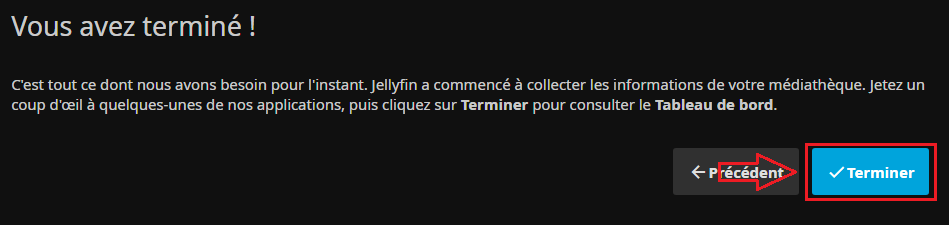
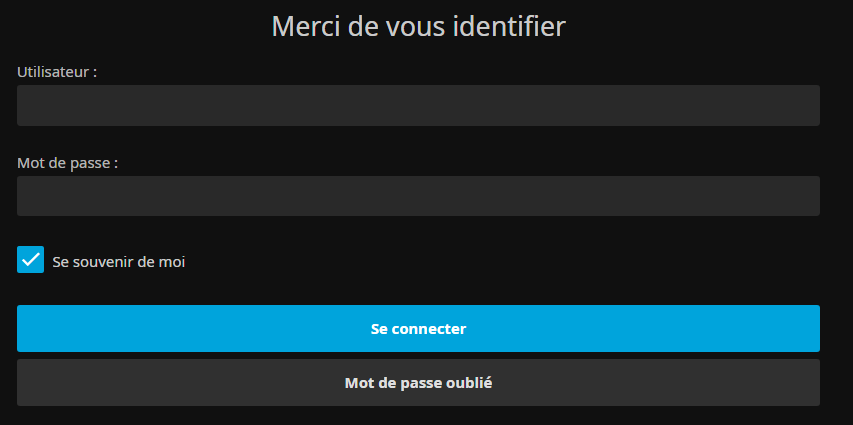
Sécurisation de jellyfin
On crée le certificat :
# openssl req -x509 -newkey rsa:4096 -keyout /etc/jellyfin/jellyfin.key -out /etc/jellyfin/jellyfin.crt -nodes -subj '/CN=localhost' # openssl pkcs12 -export -inkey /etc/jellyfin/jellyfin.key -in /etc/jellyfin/jellyfin.crt -out /etc/jellyfin/jellyfin.pfx -passout pass: # chown jellyfin /etc/jellyfin/jellyfin.pfx
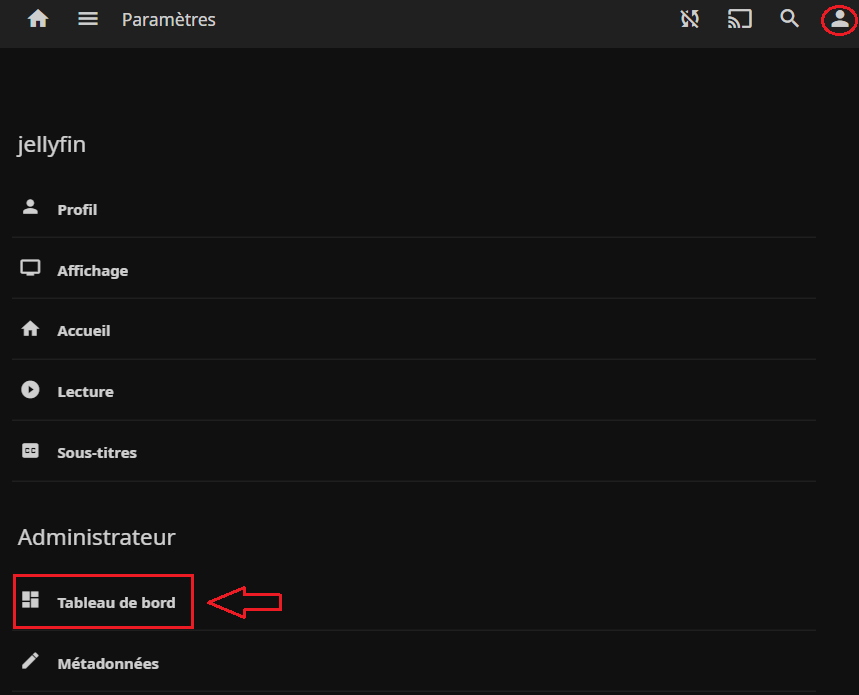
Puis on se connecte avec le compte "jellyfin" (administrateur) sur http://IP_SERVEUR:8096 et on se rend dans le tableau de bord :
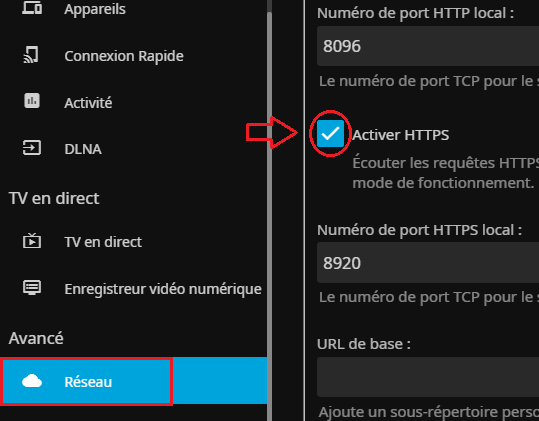
Dans le menu "Réseau" on active le HTTPS :
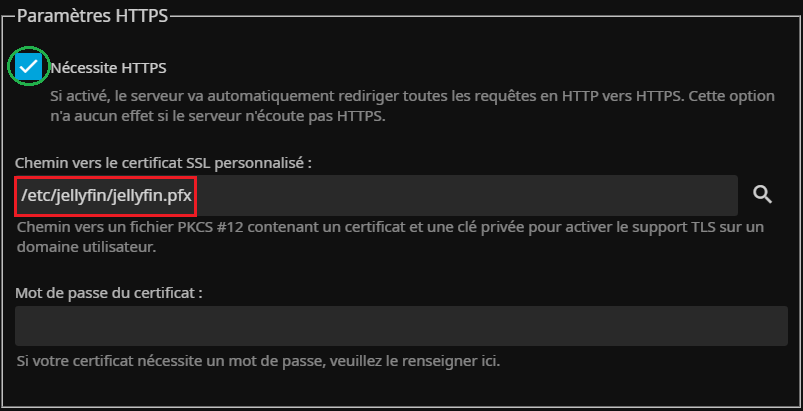
On peut forcer le HTTPS et on renseigne l'emplacement du certificat :
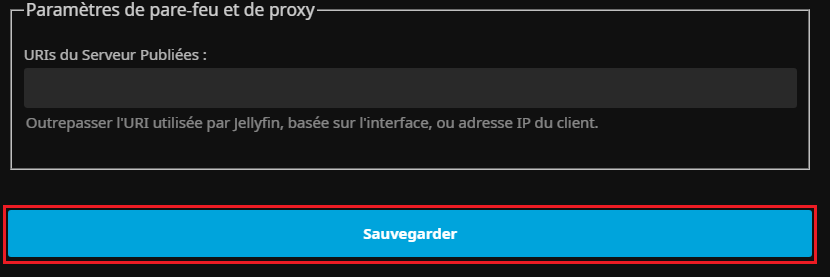
Enfin, on sauvegarde les modifications :
On redémarre le service :
# service jellyfin restart
Maintenant l'interface de Jellyfin sera accéssible via https://IP_SERVEUR:8920
Vhost pour Reverse-Proxy
server {
listen 80;
listen [::]:80;
server_name jellyfin.exemple.net;
# Uncomment to redirect HTTP to HTTPS
return 301 https://$host$request_uri;
}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name jellyfin.exemple.net;
# use a variable to store the upstream proxy
# in this example we are using a hostname which is resolved via DNS
# (if you aren't using DNS remove the resolver line and change the variable to point to an IP address e.g `set $jellyfin 127.0.0.1`)
set $jellyfin 192.168.2.209;
ssl_certificate /etc/letsencrypt/live/jellyfin.exemple.net/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/jellyfin.exemple.net/privkey.pem;
include /etc/letsencrypt/options-ssl-nginx.conf;
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem;
add_header Strict-Transport-Security "max-age=31536000" always;
ssl_trusted_certificate /etc/letsencrypt/live/jellyfin.exemple.net/chain.pem;
ssl_stapling on;
ssl_stapling_verify on;
# Security / XSS Mitigation Headers
add_header X-Frame-Options "SAMEORIGIN";
add_header X-XSS-Protection "1; mode=block";
add_header X-Content-Type-Options "nosniff";
# Content Security Policy
# See: https://developer.mozilla.org/en-US/docs/Web/HTTP/CSP
# Enforces https content and restricts JS/CSS to origin
# External Javascript (such as cast_sender.js for Chromecast) must be whitelisted.
add_header Content-Security-Policy "default-src https: data: blob:; style-src 'self' 'unsafe-inline'; script-src 'self' 'unsafe-inline' https://www.gstatic.com/cv/js/sender/v1/cast_sender.js; worker-src 'self' blob:; connect-src 'self'; object-src 'none'; frame-ancestors 'self'";
location / {
# Proxy main Jellyfin traffic
##proxy_pass http://$jellyfin:8096;
proxy_pass https://$jellyfin:8920;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Protocol $scheme;
proxy_set_header X-Forwarded-Host $http_host;
# Disable buffering when the nginx proxy gets very resource heavy upon streaming
proxy_buffering off;
}
# location block for /web - This is purely for aesthetics so /web/#!/ works instead of having to go to /web/index.html/#!/
location ~ ^/web/$ {
# Proxy main Jellyfin traffic
#proxy_pass http://$jellyfin:8096/web/index.html/$1;
proxy_pass https://$jellyfin:8920/web/index.html/$1;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Protocol $scheme;
proxy_set_header X-Forwarded-Host $http_host;
}
location /socket {
# Proxy Jellyfin Websockets traffic
#proxy_pass http://$jellyfin:8096;
proxy_pass https://$jellyfin:8920;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Protocol $scheme;
proxy_set_header X-Forwarded-Host $http_host;
}
}